Last week I looked at some of the characteristics of good passwords and used a list from Mike Chu to summarize them:
- A good password is longer than 15 characters
- No part of it exists in a dictionary of any language
- No part of it exists in any common or breached password lists
- It contains uppercase letters, lowercase letters, numbers, and special characters/symbols
Is that list the One True Path?
I should mention now that there is not uniform agreement that strictly following the above list is the best practice. Many computer security experts argue that weakening requirement #2 allows people to use nonsense phrases which might be more secure overall1 than traditional “secure” passwords.
You might skeptically remind me that last week I said that if a word is in a dictionary, then it’s on a “small”2 list and, thus, easy to crack. That is true, but this method doesn’t stop with 1 word. The key is to string 5 or even 6, 7, or 8 common but randomly chosen words together to make the password.3
For example
carrie scarf argue literal hot
If you like (or if the site’s requirements mandate it), you can then tweak the string in line with criterion #4 above by upper-casing some letters and throwing in digits and punctuation. Then you memorize the “phrase”.
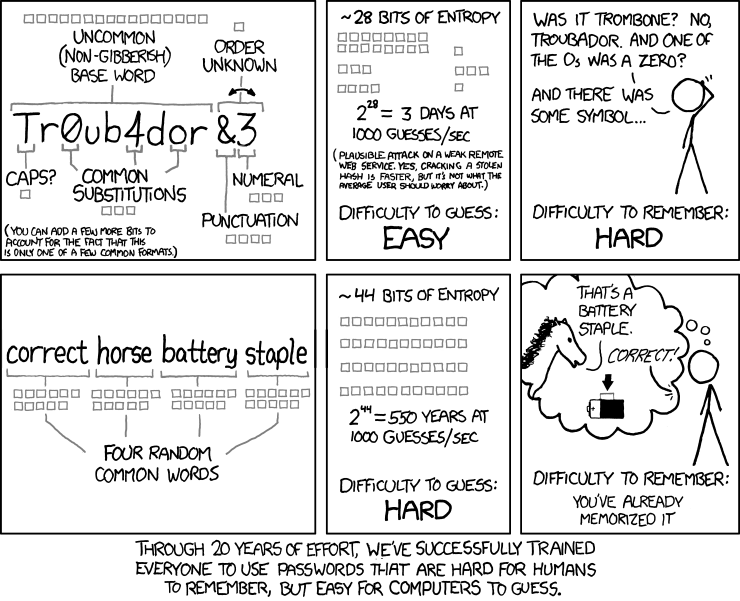
This often-shared strip from the webcomic xkcd illustrates the method and some of the theory behind it:
The phrase really should be randomly generated
In the illustration, each common word in the 4-word string is taken to have 11 bits of entropy which corresponds to selecting each word randomly from a list of about 2,000 words. If you don’t use a truly random method of selecting the words though, you can’t simply add up 11 bits per word to get the total entropy.
The point of that last paragraph was that if you think up a list of 5 words, chances are that there will be some sort of connection among them:
- Maybe they’ll form a sort-of grammatical phrase
- Or they might have related meanings
- They could easily be related to some of your publically known interests
- …
That connection reduces randomness. To avoid that, you’ll want a tool of some sort for generating random words from a list. Here are some examples (you can find others by Googling “xkcd password generator”):
- https://xkpasswd.net/s/
- https://github.com/lexcilius/xkpasswd.pm
- https://www.useapassphrase.com/
- https://passwordcreator.org/commonwords.html
Whether or not you can trust any of these tools is, as always, a question since even if the designer is trustworthy, websites can be hacked and software can be made malicious without appearing so. Thus, this method may not be quite ready for prime time, as they say, but I present it as one to consider.
Indeed, if you think of passwords as combinations for combination locks, then the problem of needing a unique password for each site we use is like that of memorizing a large number of combinations.
Next time I’ll look at software that can (metaphorically) convert that list of combinations into a keychain so that the load on your memory is much less while your security is still high.
Notes
1 For instance, one way hackers can get someone’s passwords is by surfing around Pinterest, Instagram, and other picture sharing sites looking for photos that include a victim’s computer with some of their passwords stuck to it on PostIt Notes. If you can memorize your passwords, that security hole is now plugged.
2 Small relative to what a computer can crunch through in a short time.
3 When you consider that most traditional passwords that are memorizable will probably have exactly 1 upper-case letter, 1 digit, and 1 special symbol, then a string of 5 words from a list of 10,000 or so words becomes competitive with or possibly superior to a 15-character not-quite word.
Image credits:
Locked Desktop Computer Cartoon by Free Clip Art
License: CC BY-SA 4.0
xkcd, “Password Strength” by Randall Munroe
License: CC BY-NC 2.5